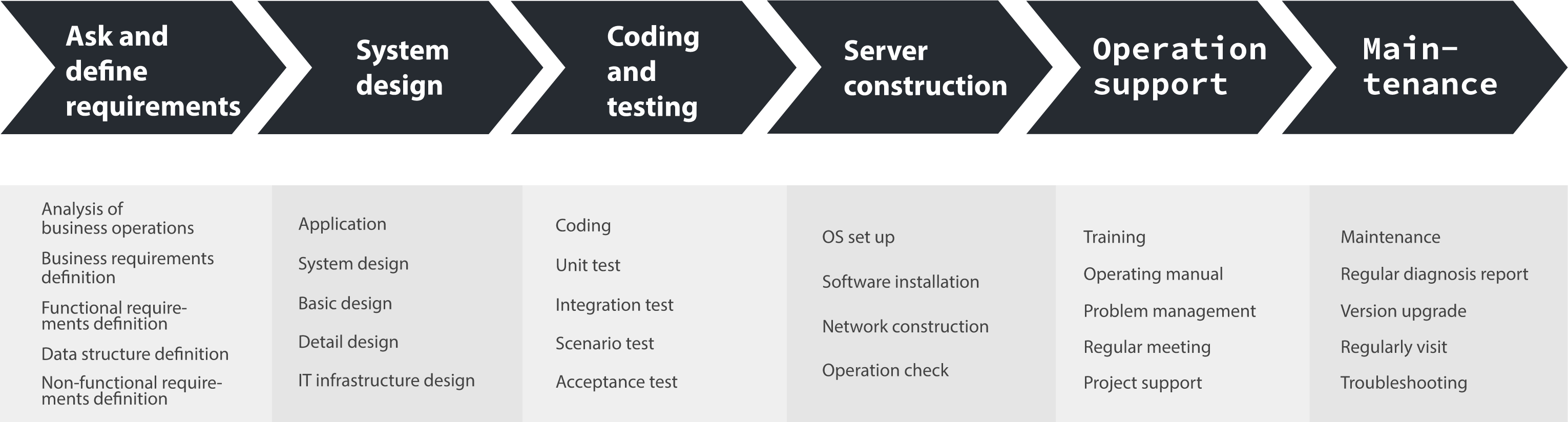
Upon implementation
On-premises
With On-premises license contract, you can build and use the system in an environment that meets your needs, such as your local machine, virtual environments, existing data centers, or cloud environments such as AWS and Azure that you are currently using, allowing you to make effective use of existing resources.
Cloud Service
The cloud service contract is for use in the "Microsoft Azure" environment (Azure usage costs are included in the service fee). You can start small and adjust the scale after the start of operation according to your situation.
- Introduction/operation consulting
- VPJ can provide consistent services from consulting prior to system implementation to post-implementation operational and maintenance support. We also focus on the maintenance system after stable operation, our support staff who understands your company's operation will provide regular reports on the system operation status to support optimal system operation.
Management Functions
-
API
Flexible system integration development with EC sites, CMS, or internal systems can be achieved as a Restful API is available.
-
Active Directory (AD) Authentication
Integrating LDAP (Lightweight Directory Access Protocol) in CIERTO allows you to better control user authorizations as well as better maintain user accounts.
-
User Authority Management
You can set access areas and operation permissions flexibly.
-
SAML Authentication Support
Supports user authentication using SAML services such as Gsuite or ADFS.
-
BI tool
Analyze the use situation of contents and can visualize it.
-
Site customization
Changes to the login screen and sidebar background color, site name, logo image, and favicon image are managed.
Security measures of CIERTO cloud
-
Security measures of the cloud platform
-
CIERTO's cloud uses Microsoft Azure, which makes it possible to run on a secure environment with various authentication methods, and regulatory features
-
ISO/IEC 27001
ISO/IEC27001 is an international standard regarding information security management systems(ISMS). This defines the structure of the organization in order to optimize information, by managing the confidentiality, information integrity, and availability of data.
-
ISO/IEC 27017
ISO/IEC27017 is a guideline for cloud services regarding information security measurements. The measurements defined in ISO/IEC 27017, enhances the general information security measurements defined in ISO/IEC27001 enabling the implementation of a security management structure compatible for cloud services.
-
ISMAP (Information system Security Management and Assessment Program)
ISMAP is a program that is purposed to streamline the installment of cloud services for government organizations. By registering/evaluating cloud services in advance that meet the security requirements of the government, a security standard for procuring cloud services can be defined for government organizations.
-
SOC Type 1,2,3 (Service Organization Control)
The assurance of the integrity for "Financial statements". SOC1 reports indicate a broad range of internal controls such as security, availability, process integrity, and confidentiality. SOC2/SOC3 targets fields other than "Financial statements".
System reference: Microsoft Azure security compliance list(https://learn.microsoft.com/ja-jp/compliance/)
-
Software security measurements
-
The latest security measurements are applied to CIERTO cloud as the development environments are scheduled/planned to be updated upon major software updates.
-
OWASP( Open Web Application Security Project)security check
OWASP is an open source software community that is active in various fields, such as hosting events, developing penetration testing tools, or creating guidelines regarding security for software/web applications. CIERTO performs software security checks according to the software/web application guidelines defined by OWASP upon software releases.
-
Penetration testing from a third party organization
Vulnerability analysis on the web application can be conducted by a third party organization according to customer needs, making it possible to apply measurements that meet the security standards of customers.
-
Security measurements during service production
-
CIERTO's cloud has various security features which makes it possible to run on an environment according to the customers security policy.
-
ACL feature
Secure access can be achieved by limiting the sender IP address and user.
-
Encryption measurements using SSL connection
Decreasing the risk of information leaks is achieved by using SSL encrypted transmission.
-
Access control according to connecting IP address
Access points can be managed by limiting the accessible IP addresses to specific locations, or offices
-
2 factor authentication
Enhancement of security by identifying individuals using authentication from a mobile device in addition to ID/ password login.
-
Management of asset access and operation history
The operation log, or access log can be managed, and exported as a CSV file.
Specification
Format for preview
- Movie
-
3gp/3g2/MP4(mp4/mp4v/mpg4)/MPEG(mpeg/mpg/mpe/m1v/m2v)/ogv/Quick Time(qt/mov)/webm/f4v/flv/m4v/mkv/mk3d/asf/vob/wmv/avi/mxf/heic
- Document
- InDesign(indd)/pdf/CAD(dwg/dxf/stl/iges)/Word(doc/docx)/Excel(xls/xlsx)/Powerpoint(ppt/pptx/ppsx/potx/pps)
- Image
- JPEG(jpeg/jpg/jpe)/png/bmp/TIFF(tiff/tif)/webp/RAW(arw/dng/orf/nef/nrw/cr2)/tga/psd/ico/PostScript(ai/ps)/heif
- Audio
- m4a/mp3/oga/ogg/dts/weba/aac/aif/aiff/flac/mka/wav/wave/wma
Recommended server environment
- OS
-
Windows Server 2019 Standard 64bit
Windows Server 2022 Standard 64bit
- CPU
- 2.4Ghz以上 4〜8core x 2 CPU
- Memory
- 16GB or more
- HDD
- The free space that is more than 100GB to a system disk
Recommended client enviroment
- Browser
-
Microsoft Edge / Chrome / Safari / (Firefox) ※latest version
- OS
-
Microsoft Windows 11 64bit Apple MacOS 10.12or later Mobile:iOS13 / Android 8or later
Reference
-
■ CPU: Intel Xeon processor 1CPU 1.8Ghz 6Core ×2
■ Memory:64GB
■ OS:Windows Server 2016 R2 Standard 64bit
■ Asset:About 1 million assets
Simultaneous access number:30-40 access
※It is just recommendation. Please give me a separately inquiry.
Contact
If you have any question, please contact us.
03-4361-2018
Monday-Friday: 9:30 AM – 5:00 PM
